TRENZ.Extensions.Infisical
1.0.4
See the version list below for details.
dotnet add package TRENZ.Extensions.Infisical --version 1.0.4
NuGet\Install-Package TRENZ.Extensions.Infisical -Version 1.0.4
<PackageReference Include="TRENZ.Extensions.Infisical" Version="1.0.4" />
paket add TRENZ.Extensions.Infisical --version 1.0.4
#r "nuget: TRENZ.Extensions.Infisical, 1.0.4"
// Install TRENZ.Extensions.Infisical as a Cake Addin #addin nuget:?package=TRENZ.Extensions.Infisical&version=1.0.4 // Install TRENZ.Extensions.Infisical as a Cake Tool #tool nuget:?package=TRENZ.Extensions.Infisical&version=1.0.4
InfisicalExtensions
This project adds extension methods for the Infisical .NET SDK to register it as a configuration provider in your .NET app.
Usage
Disable End-to-End encryption in your Infisical project settings. The .NET SDK does not support it yet:
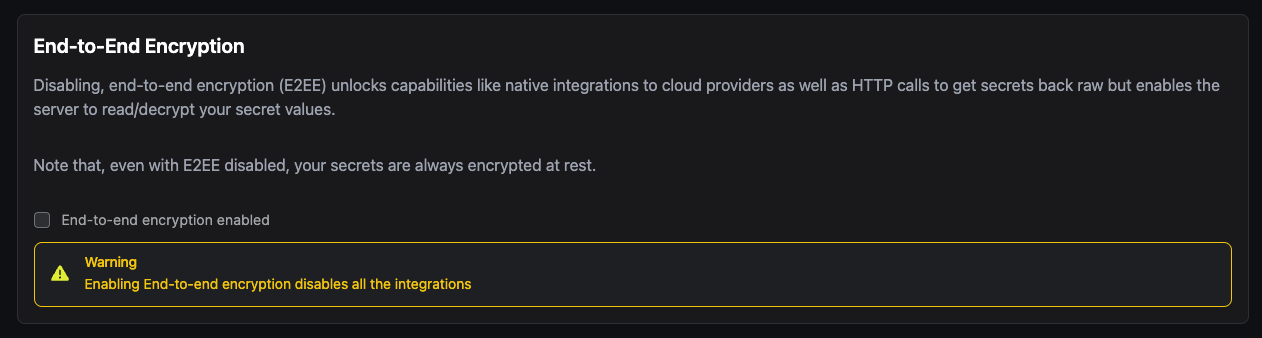
Note While you're in the settings, we also recommend to disable "Auto Capitalization"
Add your infisical settings to appsettings.json:
{
"Infisical": {
"SiteUrl": "https://<your infisical host>",
"ClientId": "07ebc18f-df32-475a-8fef-1bdd79a5c7ac",
"ClientSecret": "insert-your-client-secret",
"ProjectId": "some-project-id"
}
}
Call AddInfisicalConfiguration on your application builder:
var builder = WebApplication.CreateBuilder(args);
builder.AddInfisicalConfiguration();
// ...
This will add a InfisicalConfigurationProvider that provides all available secrets through IConfiguration.
Note The provider drops all keys in the "Infisical" object to protect your infisical credentials.
Suppose you want to store your connection string in Infisical.
You first need to add a secret in the respective environment through the infisical interface:
Note that infisical doesn't support nested secrets. The keys of the secrets need to include ":" to represent nested keys in an
appsettings.json.
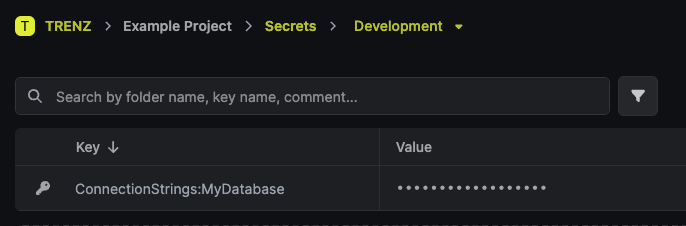
Then, in code, you can inject IConfiguration in your class and access its value as if it was in your
appsettings.json:
public class MyConnectionStringProvider(IConfiguration configuration) {
public string GetConnectionString() {
// The following call looks up the key "ConnectionStrings:MyDatabase" in IConfiguration
return configuration.GetConnectionString("MyDatabase");
}
}
You could also access the key directly using:
var connectionString = configuration["ConnectionStrings:MyDatabase"];
Polling for changes
You can let this provider regularly poll Infisical for changes. This is useful if you want to update your secrets without restarting your application.
To enable polling, you can set the Infisical:PollingInterval key in your appsettings.json:
{
"Infisical": {
...
"PollingInterval": 10000
}
}
This value is the interval in milliseconds in which the provider will poll Infisical for changes. To disable polling, just remove the key from your configuration.
The default is to not poll for changes.
Load timeout
You can set the Infisical:LoadTimeout key in your appsettings.json to specify the maximum time the provider will
wait for the initial (and subsequent) loads of the secrets.
{
"Infisical": {
...
"LoadTimeout": 10000
}
}
The default timeout is 5000 (5s).
To disable the timeout, set the value to -1.
Installation
dotnet add package TRENZ.Extensions.Infisical
License
Licensed under MIT. For more information, see LICENSE
| Product | Versions Compatible and additional computed target framework versions. |
|---|---|
| .NET | net8.0 is compatible. net8.0-android was computed. net8.0-browser was computed. net8.0-ios was computed. net8.0-maccatalyst was computed. net8.0-macos was computed. net8.0-tvos was computed. net8.0-windows was computed. |
-
net8.0
- Infisical.Sdk (>= 2.1.8)
- Microsoft.Extensions.Configuration.Abstractions (>= 8.0.0)
- Microsoft.Extensions.Hosting.Abstractions (>= 8.0.0)
NuGet packages
This package is not used by any NuGet packages.
GitHub repositories
This package is not used by any popular GitHub repositories.
# 1.0.4
- Added `LoadTimeout` to specify the timeout for loading secrets from Infisical
# 1.0.3
- Fixed issue where no keys from `appsettings.json` where available after adding infisical
- Now, all keys except `Infisical:*` are available
# 1.0.2
- Better handling for nested child keys
- Added support for `PollingInterval` to detect changes in secrets
# 1.0.1
- Fixed an issue where an invalid `AccessToken` was set on the Infisical client settings
# 1.0.0
- Initial release
- Support for adding Infisical to `IConfiguration` via `appsettings.json`